Laptop and Device Tracking
Track and locate your device fleet in real-time
Security starts with known assets. Tether maps your corporate laptops and devices in real-time, providing the intel you need to analyze and respond to any security incident.


Security starts with known assets. Tether maps your corporate laptops and devices in real-time, providing the intel you need to analyze and respond to any security incident.


Say goodbye to spreadsheets and unreliable legacy tools. The Tether agent is always-on, detects changes, and updates the admin console immediately. The result is an always-accurate view of your organization.
Collect essential IT asset management data including hardware and software inventory, and network and operating system information. Extend inventory data with custom fields.
Tether uses multiple methods to locate assets including wi-fi/cellular triangulation, GPS, MAC address correlation, and IP- geo databases from multiple providers.
Choose from pre-set report templates or create custom reports. RemoteKill® and disk encryption event logs support adherence to privacy regulation and provide crucial proof of compliance to auditors.
For an emerging security situation, use the location history UI to walk back and forth through an asset’s recent movements. Set the window of location history according to your organization’s policies.
Feed Tether data to your helpdesk, CRM or other enterprise applications with Tether APIs. Automate asset procurement and retirement procedures, eliminate double-entry and deliver accurate asset data throughout your organization.

Deauthorize lost and stolen devices on-demand or via pre-defined triggers. Protect data with emergency encryption and OS lockout.
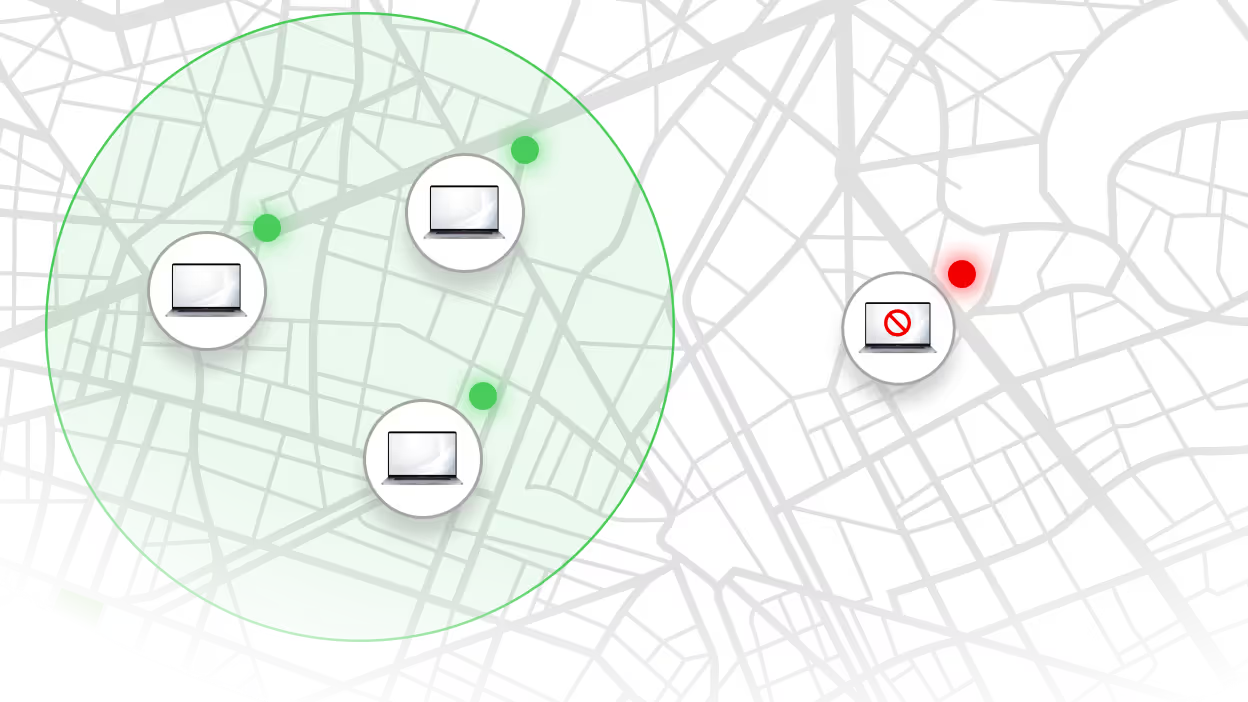
Spot undesired activities before they become incidents. Define geofences and offline curfews. Get alerts or automatically trigger RemoteKill® responses.

Encrypt all laptops by default with simple BitLocker and FileVault management. Improve helpdesk efficiency with a centralized recovery key database.

Protect corporate and BYOD devices with free, lightweight MDM.
Stand up a proof-of-concept within minutes, or book a demo with one of our IT experts.


