The best way to run a secure device fleet
Tether ensures every corporate device is tracked, encrypted and authorized for use.



Tether ensures every corporate device is tracked, encrypted and authorized for use.




Remote and hybrid work have scattered devices across countless locations and networks, creating critical blind spots for IT. Without full visibility and control, every unmanaged asset becomes a security risk.
Untracked devices are impossible to manage, resulting in poor return rates, waste, and potential security breaches.
Up to 70% of device theft involves a former employee. Data in the wrong hands can be catastrophic.
Every lost or stolen corporate laptop is a potential risk, in the form of a data breach or as a toolkit to gain access to an organization.
Mobile and remote work have introduced new concerns such as location spoofing and unauthorized foreign travel.
Organizations are required to encrypt data on laptops and devices. Many still fall short of compliance with existing management tools.
Tether has everything you need to run a secure device fleet.
Security starts with known devices. Where are your devices? Who’s using them? Are they encrypted?

Deauthorize lost or stolen devices on-demand or via predefined triggers. Protect data with emergency encryption and OS lockout.
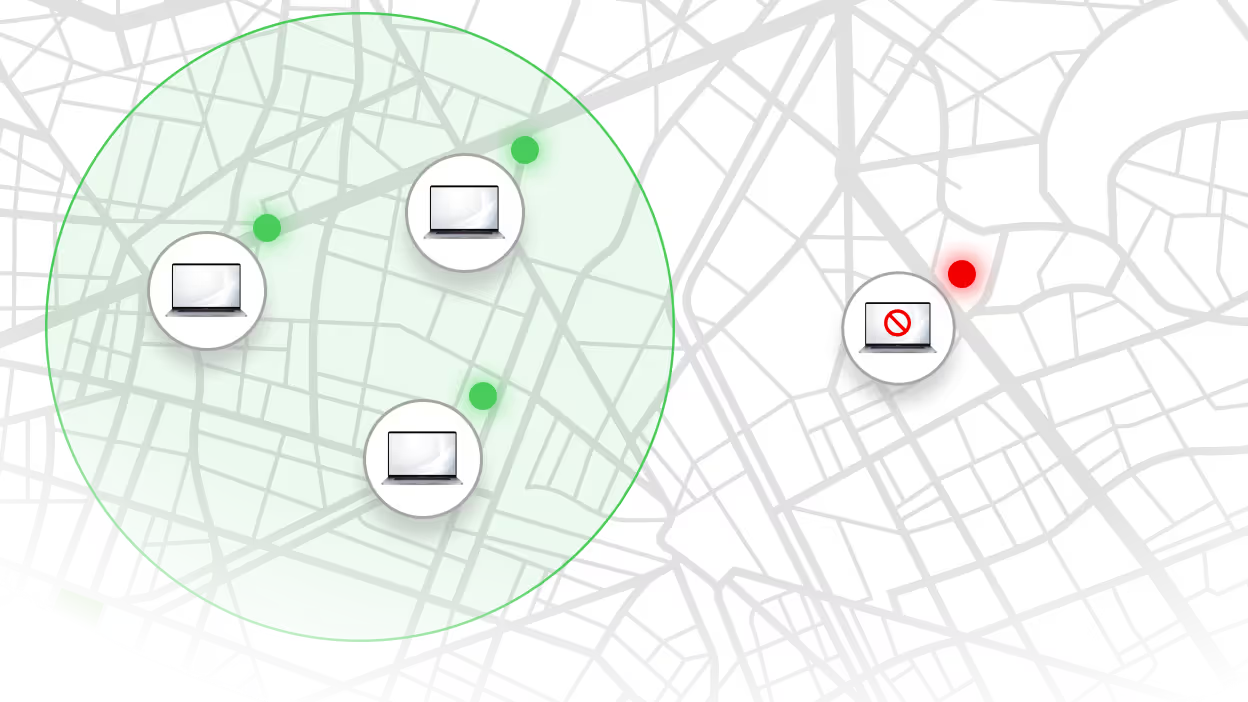
Spot undesired activities before they become incidents. Define geofences and offline curfews. Get alerts or automatically trigger RemoteKill responses.

Encrypt all laptops by default with simple BitLocker and FileVault management. Improve helpdesk efficiency with a centralized recovery key database.

Extend protection to IOS and Android devices with free, lightweight MDM.
You already protect your endpoints at the compute and cyber layer. It’s time to protect them in the real world, too.
At the messy and often overlooked physical layer, devices face risks like theft, loss, unencrypted data, and exposure to hostile networks or locations. It’s where threats occur most frequently — and where data breaches are most likely to happen.
Tether secures the physical layer — the intersection of device, location, and human behavior — providing a critical foundation for your endpoint security program.


Stand up a proof-of-concept within minutes, or book a demo with one of our IT experts.


